This Industry Viewpoint was authored by Lakshmiprasad A, Associate Director, Prodapt
Service providers in the Connectedness industry are challenged with increasing security threats as they handle sensitive data and provide critical services to customers. Security is the need of the hour as service providers target to balance rapid service delivery with adequate security measures, manage the security of complex infrastructure, including networks, servers, and cloud environments, and meet compliance requirements such as GDPR and HIPAA.
According to Cybersecurity Ventures, “More than 60% of service providers experience breaches and cyberattacks. Cybercrime damages cost $6 trillion globally, and the cost is expected to increase by 15% per year over the next five years. Due to these increasing threats, the traditional approach where the security is bolted at the end of the development process, is no longer effective.
In addition, traditional security approaches lack the following:
- Mechanisms to handle agile developments leading to a fragile and vulnerable code
- Sophisticated security measures for new services that are beyond the perimeter
- Techniques to secure the evolving ecosystems such as Kubernetes and observability tech stack which are prone to attacks
To overcome these challenges, service providers must enable and prioritize continuous security by infusing security at every stage of the software development lifecycle. This establishes trust in application usage and accelerates quality releases.
This article elaborates on how service providers can leverage DevSecOps for faster delivery of secure products.
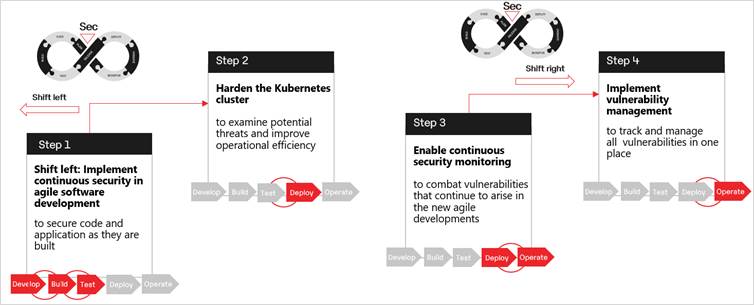
Fig: The four-step approach for successful DevSecOps implementation
The four-step approach to implement DevSecOps and accelerate secure product releases:
- Shift left: Implement continuous security in agile software development
The shift left approach in security facilitates the identification and resolution of defects early in the software development lifecycle, improving code quality and reducing costs.
While developers try to secure the code and application as they are built, there are four key components to look for:
- Open-source/Third-party libraries: Scan open-source packages using Software Composition Analysis (SCA) tools such as Dependency-check and npm to mitigate risk and secure application health. Further, integrate the SCA tools into the CI/CD pipeline to enable automatic scanning of vulnerabilities
- Application code: Implement tools like SonarQube and Bandit to inspect the code quality continuously and highlight the newly introduced issues. Integrate SonarQube with CI/CD platforms like Jenkins which enables automated security scanning and execution of unit test cases with every build, thus saving time and effort
- Endpoints: Leverage Dynamic Application Security Testing (DAST) tools such as OWASP ZAP and Burp Suite to identify vulnerabilities in web applications automatically
- Containerized applications: Implement vulnerability scanning tools such as Trivy and Clair to scan docker images, IaC scripts, vulnerabilities in OS packages, and sensitive information
- Harden the Kubernetes cluster
Kubernetes clusters require proper configuration and hardening to secure the infrastructure, reducing the attack surface. By hardening the Kubernetes cluster for customer-facing applications, service providers can deploy strict access controls, network policies, and regular updates to safeguard customer data and applications from potential security breaches.
Below are a few recommendations to harden the Kubernetes cluster and improve operational efficiency.
- Implement Kube-bench to adhere to Center for Internet Security (CIS) benchmarks and deploy Kubernetes cluster securely
- Leverage Kubescape to harden the Kubernetes cluster by evaluating it against MITRE ATT&CK matrix
- Implement tools like Kube-score and KubeLinter to identify insecure configurations in Kubernetes YAML files and Helm charts before deployment into a Kubernetes cluster
- Leverage tools such as Falco and Docker bench to continuously monitor and identify runtime security issues
- Enable continuous security monitoring
With the rising threats in agile development environments, uninterrupted monitoring of critical assets has become vital to detect and mitigate potential threats in real time. Continuous security monitoring helps service providers gain real-time visibility into the security posture of their systems and enables proactive identification and response to security threats in container environments and orchestration platforms.
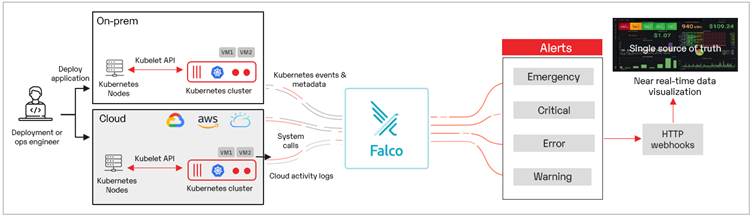
Fig. Sample flow of continuous security monitoring with Falco
Recommendations:
- Implement Falco to detect unexpected behavior, configuration changes, and data theft in real-time across containers, cloud, and Kubernetes audit logs
- Gain a real-time view of vulnerabilities by integrating Falco with incident response workflow systems through Alert Manager and Webhooks
- Perform periodic scanning of open-source packages to safeguard the application from recently exploited cyberattacks
- Implement vulnerability management to track and manage all vulnerabilities in one place
As service providers struggle to combat vulnerabilities in their IT environments, they need a real-time view of performance and security issues. Leveraging a centralized vulnerability management dashboard saves the time and effort of service providers in figuring out how a vulnerability affects the production environment and which systems are affected.
Recommendations:
- Implement vulnerability management tools like DefectDojo to integrate DevOps and continuous security. It further helps in managing and tracking vulnerabilities
- Develop unique reports to understand exactly when new vulnerabilities are introduced in a build or remediated
- Configure remediation timeframes based on the criticality of findings, which helps with reminders for remediation
Conclusion
The four-step approach, as explained in this article, enables continuous integration, faster delivery of secure products, and reduction of compliance costs. It also provides the following benefits:
- 80% reduction in vulnerabilities
- 2x faster and more secure product releases
- 70% reduction in security incidents, optimizing OpEx
I appreciate the efforts of my colleague Priyankaa A- Senior Analyst, Strategic Insights, for her contribution and continuous support in shaping this article.
Author Bio
Lakshmiprasad A
Lakshmip rasad is a hands-on seasoned technology leader with over 15 years of experience in leading strategic architecture transformations data analytics and migrations, product design, UX design, enterprise-wide DevSecOps, and CI/CD initiatives. He has successfully defined and delivered digital transformation programs, partnering with C & D-level leadership for globally leading telcos/digital service providers.
rasad is a hands-on seasoned technology leader with over 15 years of experience in leading strategic architecture transformations data analytics and migrations, product design, UX design, enterprise-wide DevSecOps, and CI/CD initiatives. He has successfully defined and delivered digital transformation programs, partnering with C & D-level leadership for globally leading telcos/digital service providers.
Lakshmiprasad is a digital transformation leader at Prodapt, the leading consulting, technology, and managed services provider to the Connectedness vertical. Prodapt’s customers range from telecom operators, digital / multi-service providers (D/MSPs), technology, and digital platform companies in the business of Connectedness. Prodapt builds, integrates, and operates solutions enabling DSPs on their transformation journey at several layers, including cloud, customer experience, business outcome-focused initiatives, CapEx, and OpEx optimization programs.
If you haven't already, please take our Reader Survey! Just 3 questions to help us better understand who is reading Telecom Ramblings so we can serve you better!
Categories: Industry Viewpoint · Security · Software





Discuss this Post