This Industry Viewpoint was authored by Tony Kourlas, Director, IP Product Marketing for Nokia
Sir Isaac Newton once observed that for every action there is an equal but opposite reaction. Set something in motion to fulfill a purpose but be prepared for the pushback this action will create. This comes as sage advice for mobile providers preparing their transport networks for 5G. Take advantage of the flexibility and openness that are integral to 5G but be prepared for the increased security risks that come along with these benefits.
If you didn’t feel a chill wind blowing at the simultaneous mention of security and mobile transport, you are not alone. In traditional mobile networks, private lines connected regional RANs to a centralized core making transport security a de-facto feature of the network architecture itself. Threats typically came from outside this perimeter – from infected subscribers targeting internal infrastructure, or from DDoS attacks targeting the internet-attached core. So, it’s no surprise that mobile security discussions tended to focus on these areas.
The conversation started to change with the advent of 4G. Security holes began to appear as providers began sizing up IP and third-party networks for mobile transport. IP routers made RAN aggregation far more flexible and cost-effective, enhancing the quality and performance of mobile services while reducing operational complexity and cost. Third-party networks extended a provider’s reach and provided a more economical way of securing additional bandwidth. The trade-off was an increase in attack surfaces. Traffic that flowed through third-party networks became more vulnerable to theft and manipulation, and the secure core and RAN sites at either side of these third-party network connections were suddenly open to external breach.
The solution was to leverage IPsec, a secure network protocol suite, to secure the IP backhaul links that connected regional RANs to centralized cores. IPsec provides three essential functions to secure a link: authentication, integrity and confidentiality. Authentication ensures that the sender and receiver are who they say they are. It checks the authenticity of certificates during IPsec tunnel setup using a mutually trusted certificate authority. Data integrity is assured by authenticating packets sent by either side to ensure they have not been altered in any way, and confidentiality is ensured by IP packet encryption. Together, the three IPsec functions closed the security holes opened by the new 4G transport options.
But if 4G has managed to open the door to security risks, 5G has blown it away all together. The difference between the two is primarily based on scale and complexity. The highly distributed and virtualized nature of 5G, combined with a large influx of radio sites, has created many additional vulnerabilities and entry points that attackers can exploit.
In 5G, network and service functions are no longer captive to specific sites or form factors. They are distributed and placed anywhere they need to go to optimize capacity, latency and reliability. Control plane and user plane functions enjoy a similar liberation. They are disaggregated and deployed wherever needed to minimize cost and optimize performance. For the core, this means the creation of a new edge cloud with select user plane and service functions moving from centralized sites to regional sites where they can get closer to customers. For the RAN, the traditional radio unit, distributed unit and centralized unit (RU/DU/CU) architecture is decomposed to individual DU and CU functions that can be distributed to regional data centers to leverage cloud economies of scale.
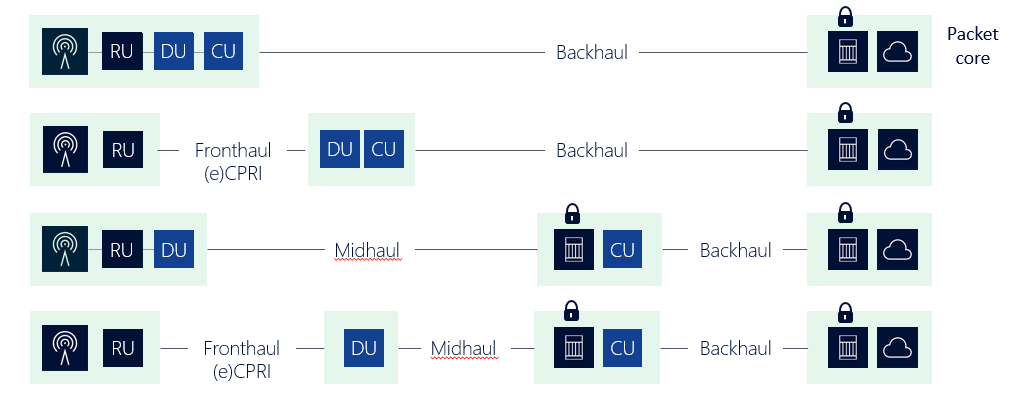
Figure 1 illustrates only a fraction of the new combinations enabled by this new transport architecture. Securing 5G transport requires protection for backhaul links that connect the CU to the core, midhaul links that connect the DU to the CU, and fronthaul links that connect the RU to the DU. Any or all of these approaches can be deployed in a single network, depending on the 5G architecture choices made, and the need for concurrent 2G/3G/4G support. IPsec gateways are required to protect both the backhaul and midhaul links, while fronthaul leverages enhanced Common Public Radio Interfaces (eCPRI) with or without Media Access Control security (MACsec).
So, while 5G network architecture entails significant changes to 4G, the underpinnings of how IP transport security is accomplished are essentially the same – it’s the scale, density and complexity of 5G transport that transforms security from a peripheral issue to a critically important one. This rethink is bolstered by additional security trade-offs made deeper in the network. The widespread use of open technologies – from cloud servers to IP protocols – introduces even more attack surfaces that if left unchecked, can transform a transport breach into a catastrophic failure. Escalating state player interference in mobile networks is yet another factor that is raising the profile and importance of securing transport.
If you are starting to feel a chill wind blowing, the good news is that vendors are already up to the challenge. There are solutions out there that have cut their teeth in public 4GE/LTE networks with no breaches recorded over the full decade of their deployment. These solutions are now being deployed in 5G and public safety networks to protect providers from the inevitability of Newton’s third law.
 Tony Kourlas has more than 25 years of experience working in product management and product marketing roles within the telecom industry. He’s been with Nokia for over 10 years, working in product marketing for the company’s IP/Optical Networks business group.
Tony Kourlas has more than 25 years of experience working in product management and product marketing roles within the telecom industry. He’s been with Nokia for over 10 years, working in product marketing for the company’s IP/Optical Networks business group.
If you haven't already, please take our Reader Survey! Just 3 questions to help us better understand who is reading Telecom Ramblings so we can serve you better!
Categories: Industry Viewpoint · Security · Telecom Equipment · Wireless





Discuss this Post