This Industry Viewpoint article was contributed by NetEvents
Recent discussions around SDN and cloud security track the development of networking from software-defined to business-defined.
The 2015 Cloud Innovation Summit in San Francisco included a session on “Software Defined Cloud Networking” chaired by IDC’s Director of Research for Datacentre Networking, BradCasemore. When buzzwords collide I am reminded of those wonderful Hubble Telescope images of merging galaxies, but in this case the merger is not unexpected; as Casemore put it: “You could make a case that there wouldn’t be any need for SDN without Cloud”.
His first point was about the change in his role: not long a go a presentation on networking would have been about “protocols and the mechanisms and so forth” and treating the network as a detached and separate silo. Now his focus is more on the context, what is happening where and why.
Turning to IDC data, he pointed out that 80% of US companies are at least considering private or public cloud. Those using cloud expect to increase their cloud spending by 34% over the next 24 months business expects to spend some $122b on Public cloud services in 2018. Another important factor from a developer’s perspective was that 90% of new commercial apps are now developed specifically for the cloud – underlining his point that networks exist to support critical workload, they do not exist in a world to themselves.
As to the changing role, he went on to talk about the cloud as a key pillar of what he called “the third platform”. The first period (1980 to 1995), the first pillar of networking, was about networking for mainframes and mini computers: think ARPANET, circuits, hubs, SNA, Ethernet, Token Ring and Routers. The second period (1995-2010) was about the early days of switching and multiprotocol routing in LAN/WAN technologies: think switching, multiprotocol routing, LAN-WAN, TCP/IP and PC/client server with predominantly north-south traffic.
The third period, starting around 2010, is networking for third platform applications: SDN/DDI and other architectural approaches. Think about a network that’s DevOps and, at least, developer friendly. It’s about hybrid cloud, virtual workloads and workflows, big data, VMs and containers – with a focus on automation, programmability and orchestration in this world where east-west traffic predominates.
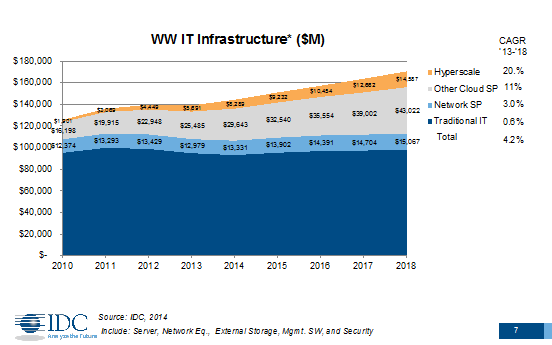
Casemore’s seventh slide (Fig 1) reminds us that, for all the talk about Cloud, traditional IT still dominates the spend. But the point is where the growth lies, and Hyperscale operations likeFaceBook, Google, Amazon and Microsoft lead the field at 20% CAGR. He says that it is not just in financial terms that the hyperscalers are leading the field: “There have been innovations out of hyperscale that are making their way down market. They may not be used in the same manner as they make that migration. They’ll be repackaged in many cases. But I think those innovations are critical. They’re having an impact not only for other cloud providers, enterprises and service providers, but they’re also having certainly significant implications for the supply chain in the networking industry.”
The business need
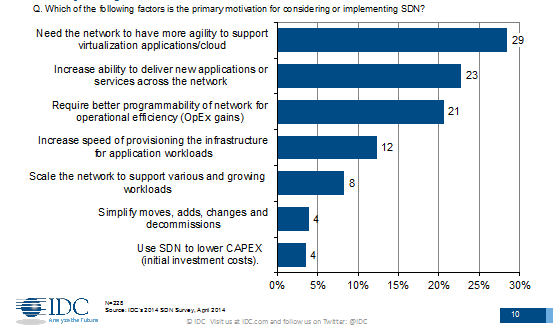
What does business want from these new developments? What is driving today’s SDN deployments? The following survey results are in response to IDC asking “Which of the following factors is your primary motivation for implementing SDN”. Because the question requires a single selection, the percentages drop off more steeply than one might expect, but the key requirement stands out: Needing the network to have more agility to support virtualisation applications in cloud was top at nearly 30%. Increasing the ability to deliver new applications or services 23%. Requiring better programmability of the network for operational efficiency and OpEx gains, again over 20% and so on.
In the case of large network operators, Infinera’s Chris Liou, Vice President Network Strategy, says that their customers are looking for one of three main business objectives: 1) to be able to innovate and develop new service offerings they can offer to their customers; 2) to help streamline the management of their own optical infrastructure; or 3) to optimize the transfer of services between datacentres and locations. As an example of the first he mentions Pacnet providing datacentre connectivity services in the Asia Pacific region: “Their enterprise customers are increasingly interested in being able to order bandwidth services on demand between datacentres rather than being subject to long-term lease requirements.”
This emphasis on the business benefits is echoed by Citrix’s Graham Melville, Senior Director, Product Marketing for Netscaler, who points out that networking’s first phase was originally well focused on business benefits and sharing resources such as expensive laser printers. What then happened was that networking grew increasingly concentrated into a specialist department with its own agenda, and it was SDN that has knocked down those walls and is beginning to open things up to create what will be called “Business Defined Networking”.
Spirent CEO, Eric Hutchinson, suggests that this will give service providers a massive business opportunity to provide a whole raft of very flexible cloud services to small to medium sized enterprises. Those customers have not been fast to embrace SDN themselves, because they do not understand the technology sufficiently, but they would be attracted to the right business-oriented service offering. To win them over they would, however need the reassurance of performance, reliability and security guarantees that can only come from thorough test and monitoring. Another reassurance would be the acceptance of standards for NFV that OpenCloud Connect is working on.
The security hurdle
Dave Hawley, HP’s Global Product Manager, agrees that security is a big concern: “I think there is both a misunderstanding and an opportunity here because ultimately cloud architectures provide privacy and multi-tenancy and are inherently more secure than a traditional datacentre. The cloud and SDN architecture separates workloads in a way that you could never do in a traditional datacentre. However, you still need to look for intrusions… the security team is trusted to ensure that any type of intrusion into their network, or any type of threat can be detected and I don’t think we’ve done a good job of building that into the same architecture. So, that’s another challenge for enterprises that want to shift their mission critical functionality onto a cloud. How do I make sure that I’m not just opening myself up to a different set of risks?”
Eric Hutchinson pointed out also that: “Cloud actually offers the ability to take security to another level because you can take a global database of all the malware… You can be much more responsive.”
Nand Mulchandani, Vice President, Citrix, added: “when I was running security products at VMWare, we broke the security problem down into components. There is security of the platform; there is the operational security of the cloud provider; and then there is the actual security with the applications running on the infrastructure – three different things. The platform itself is probably more secure at a service provider than your own internal IT because the best practices and dedicated people with a lot of domain expertise etc.” On the other hand there is the doubtful security of applications exposed on the public Internet, or with a misconfigured firewall: “If you’re operating in the little castle of your own enterprise, you’ve got it hardened and can run applications that are not as hardened or well written inside that shell. Then there is obviously the data sovereignty issue – not only from a snooping perspective”.
“Ultimately, I see the development of security as a service” responded Eric Hutchinson. “In the cloud you can capture and collate so many of the issues, attacks and varieties. You start to recognise malware before it attacks you because criminals are lazy and reuse code as much as possible. You can give people enhanced security before you suffer the attack, and that makes the cost of attacking more expensive for the attacker”. Indeed, Security as a Service is already being promoted by Wedge Networks under the trademark Cloud Network Defense.
…And so to Business Defined Cloud Networking
A month after the Global Cloud innovation Summit and Brad Casemore’s debate, there was a round table discussion on “Business Defined Cloud Networking” at the NetEvents APAC Press & SP VIP Summit. The Chairman, Manek Dubash, began by reiterating some of the material that Casemore had presented, then introduced Derrick Loi to the panel. Derrick is Senior Director, DC Solution and Services, Orange Cloud for Business APAC, from Orange Business Services (OBC).
One of the key points that had come up in the previous debate was the proliferation of clouds: first the public cloud and then, as the technology caught on, there were large organisations creating their own internal private clouds to gain the benefits of greater agility and cost savings, while avoiding some of the security issues in connecting to a public cloud. Next the rise of virtual private clouds hosted by cloud providers and the mix of all these types of cloud led to hybrid cloud solutions shaped very much to the business, its applications and the different flavours of reliability, security and compliance that are required by large operations.
The term “Business Defined Cloud” is very appropriate for such hybrid solutions, but how well do they work? The main driver for the OpenCloud Connect forum has been concern about the future need to integrate different clouds, and the need for open standards to make this possible when, for example, merging organisations want to merge their cloud operations. Such standards have not yet been finalised, so what sort of problems arise when different cloud services need to be integrated in a hybrid cloud? What can be done to unify authentication, end-to-end performance reporting, charging for usage and so on?
Derrick Loi explained how OBS was addressing this problem: “What Orange has done is come up with our multi-cloud orchestration platform, in short MCOP. The unique value proposition of this platform is that it serves as a single console to automate the provisioning of applications, workloads and VMs across multiple cloud profiles. And with this platform you can now also move workloads between clouds. For example, a non-mission-critical application initially could be hosted on AWS or any public cloud providers. But as it becomes mission-critical, you need a secure and automated process to transport the workload back into a private cloud or a virtual private cloud. And this is part of the capabilities that we provide.”
How can the enterprise ensure an end-to-end SLA when using third party cloud services? “We have come up with an offer called Business VPN Galerie – an extension of our Business VPN, incorporating the cloud services into the enterprise VPN. How it works is that for all the third party cloud services, we have established a local cross-connect at the nearest POP between our customer virtual router from our MPLS IPVPN, with the third party cloud services edge router. All the customer has to do is subscribe to a business VPN Galerie port on our PE router. And from there, the relevant virtual circuits or the VLANs will be established to the third party cloud service provider. They can now enjoy an end-to-end SLA even when using third party cloud services.”
If this sounded like the total solution, the end of all the world’s cloud integration problems, then panellist Gint Atkinson, KVH’s VP Network Strategy & Architecture, threw a spanner in the works by reminding us that it was one thing to integrate the technology between two systems, and quite another to integrate the business cultures and processes involved. “Colt and KVH at the engineering level were effectively integrated a long time ago. We had our two identical platforms, different service definitions but same service platform, same global engineering.” But as soon as they tried to integrate the business processes and figure out how order flow-through was going to happen from London to Tokyo as an integrated company instead of two separate orders, they hit problems: “On the network it was transparent but now how do we integrate the ordering systems and the trouble ticketing systems and everything else. The amount of stress that that produced was shocking. At the business process level there are massive issues on how partners are going to effectively work together.”
This is, of course, the second part of the challenge facing OpenCloud Connect: not just to set standards for the interfaces and technologies, but also for the business definitions and practices that will be shaping tomorrow’s cloud.
Business has indeed started to define the clouds that it needs but, until there is an agreed business language, no amount of cloud integration and orchestration will guarantee success.
If you haven't already, please take our Reader Survey! Just 3 questions to help us better understand who is reading Telecom Ramblings so we can serve you better!
Categories: Ethernet · Industry Viewpoint · NFV · SDN






Discuss this Post